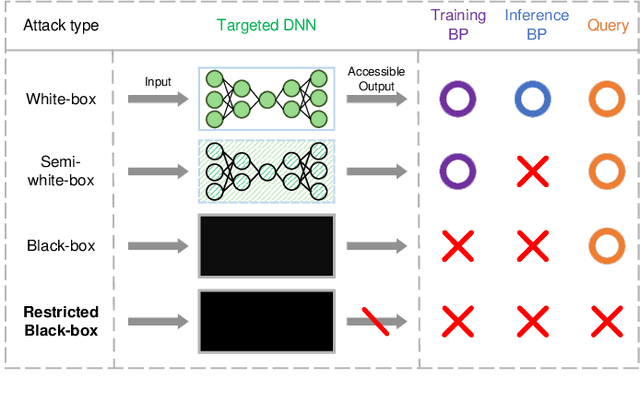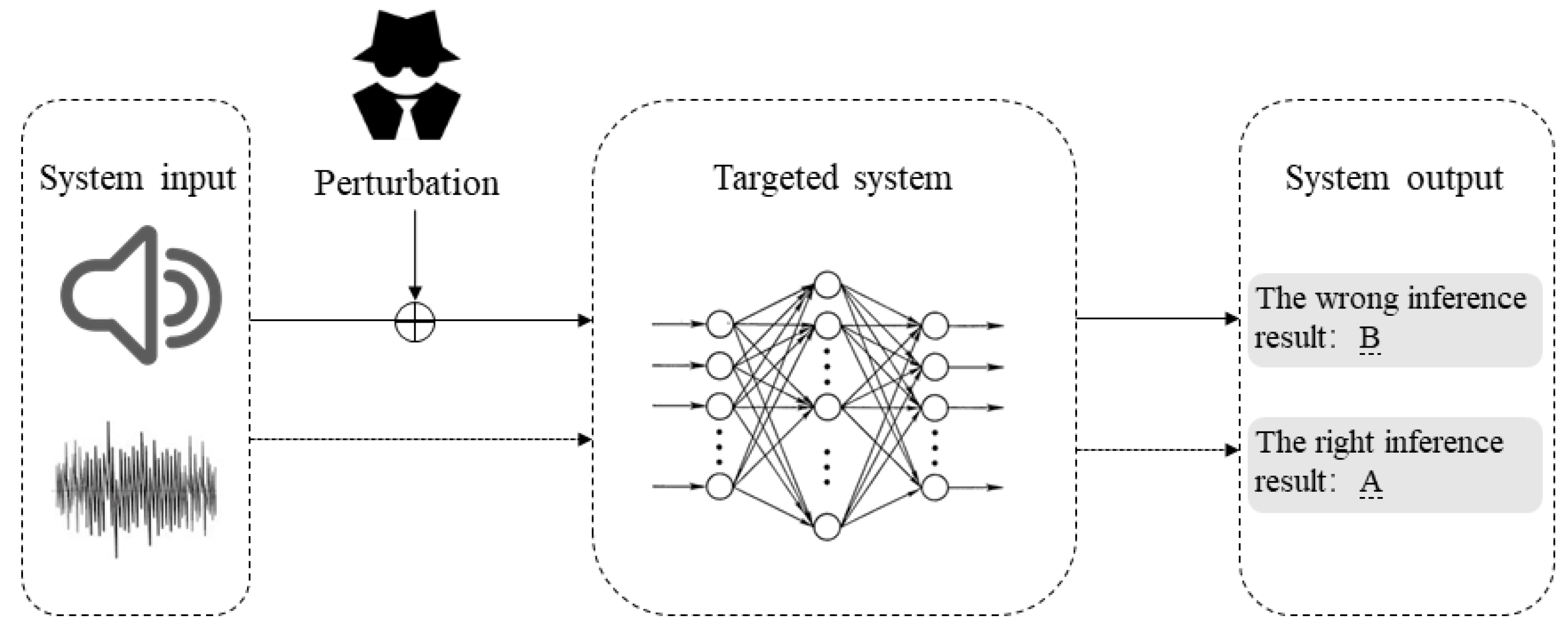
Applied Sciences | Free Full-Text | Adversarial Attack and Defense on Deep Neural Network-Based Voice Processing Systems: An Overview
Learning Machine Learning Part 3: Attacking Black Box Models | by Will Schroeder | Posts By SpecterOps Team Members
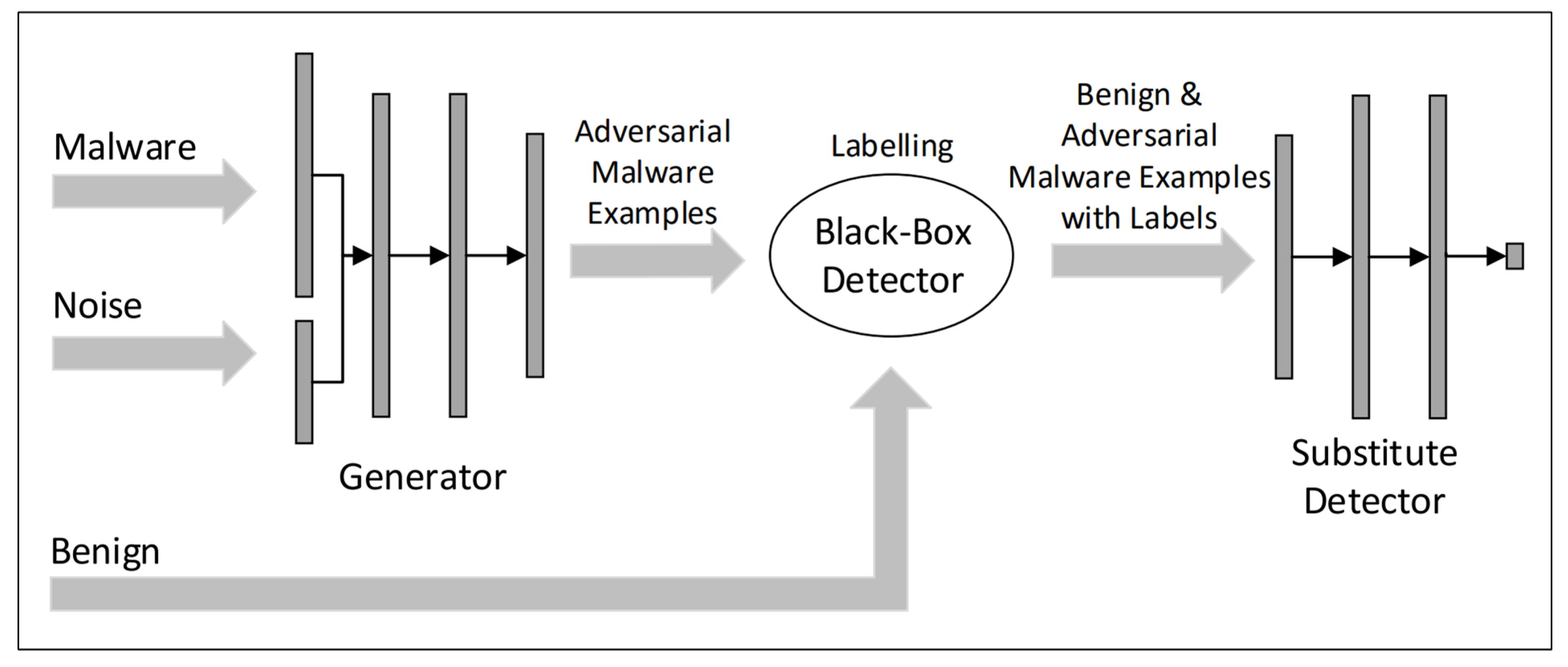
Applied Sciences | Free Full-Text | Review of Artificial Intelligence Adversarial Attack and Defense Technologies

arxiv on Twitter: "Hybrid Batch Attacks: Finding Black-box Adversarial Examples with Limited Queries. https://t.co/00xvLX0ota https://t.co/oul0ht42A7" / Twitter

FE-DaST: Fast and effective data-free substitute training for black-box adversarial attacks - ScienceDirect

python - which attack in cleverhans is grey box attack and which is white/black box attack in cleverhans library? - Stack Overflow
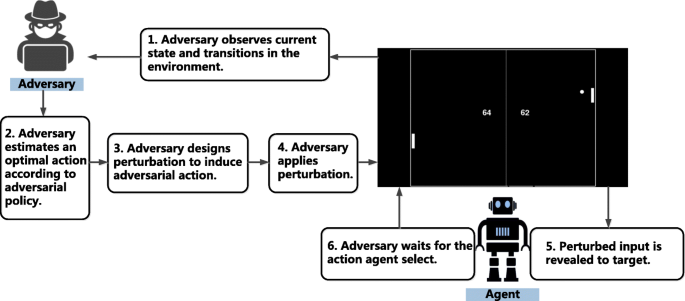
Adversarial attack and defense in reinforcement learning-from AI security view | Cybersecurity | Full Text

python - which attack in cleverhans is grey box attack and which is white/black box attack in cleverhans library? - Stack Overflow

Proposed method for black-box adversarial attacks in autonomous vehicle... | Download Scientific Diagram

![Black-box adversarial attacks on videos Patent Grant Jiang , et al. Sept [Fudan University] Black-box adversarial attacks on videos Patent Grant Jiang , et al. Sept [Fudan University]](https://uspto.report/patent/grant/10783401/US10783401-20200922-D00000.png)
![PDF] Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN | Semantic Scholar PDF] Generating Adversarial Malware Examples for Black-Box Attacks Based on GAN | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/86e5827087e11dc929d592ee7b3d7581fc48265e/3-Figure1-1.png)