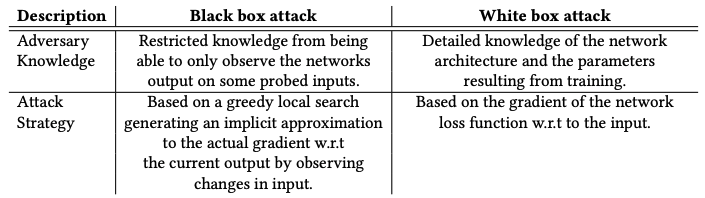
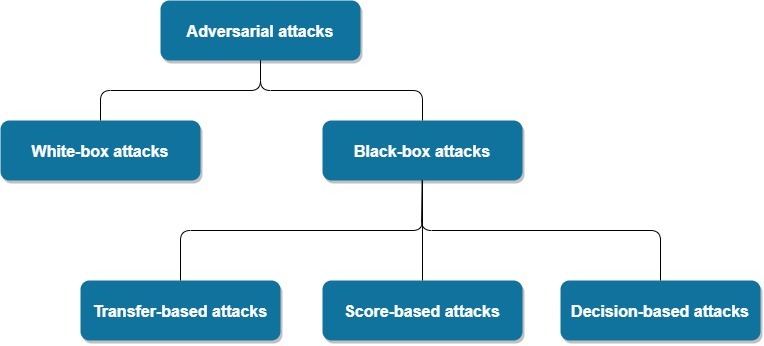
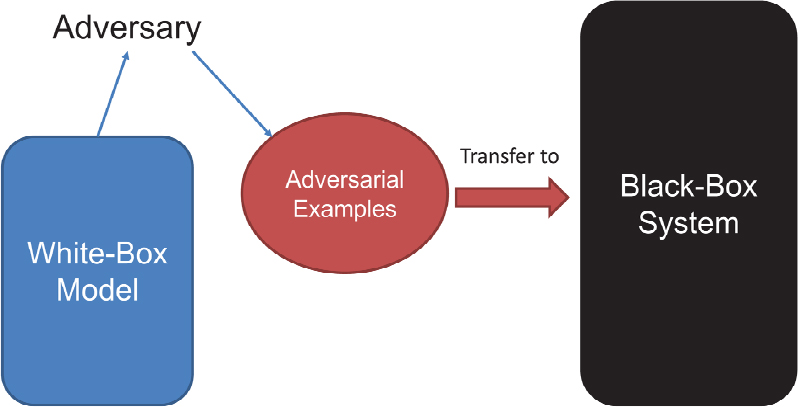
AutoZOOM : Background and Methods 3 . 1 Black-box Attack Formulation and Zeroth Order Optimization | Semantic Scholar
Learning Machine Learning Part 3: Attacking Black Box Models | by Will Schroeder | Posts By SpecterOps Team Members

How to hack Wincor Cineo ATMs to bypass black-box attack protections and withdraw cash - Tunisian FinancialCERT
ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models
7 Plenary Session | Robust Machine Learning Algorithms and Systems for Detection and Mitigation of Adversarial Attacks and Anomalies: Proceedings of a Workshop |The National Academies Press
ZOO: Zeroth Order Optimization Based Black-box Attacks to Deep Neural Networks without Training Substitute Models
Architecture overview of distributed black-box adversarial attack using... | Download Scientific Diagram

FE-DaST: Fast and effective data-free substitute training for black-box adversarial attacks - ScienceDirect
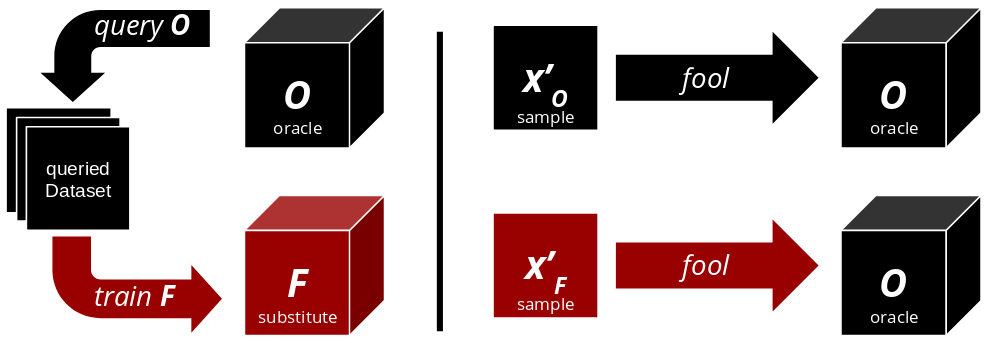
Institute for Applied AI - Selected Topics in Deep Learning - #1 Adversarial Attacks: C3 Black-Box Attacks